Let me start with Network Security in Azure.
There are various ways to secure your Virtual network in Azure.
- Network Security Groups (NSG): a NSG is a set of Allowed and Deny rules for Inbound and Outbound connectivity. There are some default Allow and Deny Rules also setup which can not be deleted or Disabled. If you want to override a specific Default Rule, then you can add another Allow / Deny Rule with a greater priority. The Priority of NSG rule is processed from lower number to higher number. So Effectively a Rule with lower Number has greater priority.
- Firewalls: Network Perimeter security can be enforced by using Azure Firewall and creating a set of NAT rules (SNAT or DNAT both can be used with Azure Firewalls).
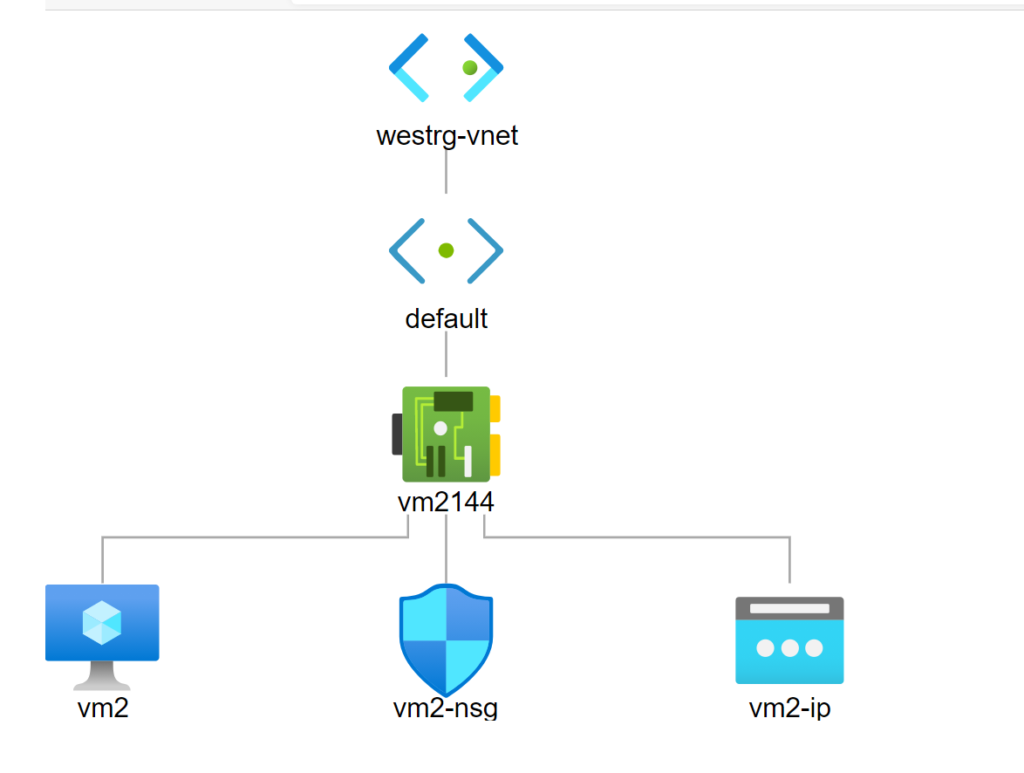
Network Security Groups
Functionally a NSG can be associated with NIC (Network Interfaces) or Subnets (in a Virtual Network).
- Subnets - All the Virtual Machines in the Subnet follow the Rules specified in the NSG associated with the Subnet.
- NIC (Network Interface) - the NSG rules specified are applicable to individual Virtual Machine to which the NIC is attached.
Suppose there are 2 different NSGs NSGSubnet and NSGNIC. NSGSubnet is associated with a subnet "Appsubnet" and NSGNIC is associated with NIC VM1Nic which is for VM1. The VM1 is still in the same Subnet AppSubnet. In this case the Flow processing happens serially and the traffic is allowed only when both of the NSGs are allowing the traffic.
SSH connectivity is allowed for all the VMs in the AppSubnet by creating a "Allow_SSH_Port" rule in Inbound Rules with Priority greater than DenyAllinBound rule in NSGSubnet. However, if you want to restrict a particular VM to not allow SSH connectivity, then you can create another NSG as NSGNIC and associate it with the VM's NIC. This will protect your specific VM only.
Network Security Groups can be Setup in multiple ways as below with any combination of below type of Rules.
- IP Based - Specify Source and Destination IP Addresses with or without Ports
- IP Subnet / Network / Virtual Network based - Specify Subnet as Source and Destination in CIDR format.
- Service Tags - Azure uses various Azure Service TAGs to identify and group different types of Azure Services. These Service Tags can be used as Source or Destination to specify the Allow / Deny Rules
- Application Service Groups - Groups multiple VMs based on their Responsibility or Environment. Efficient way to Segment your Virtual Networks on Azure.
Application Service Groups
The Application Service Groups can be created and attached to different VMs based on their Roles. Like Web Servers can form WebserverASG, while DB Servers can be in another ASG as DBServersASG, etc. The ASGs allows you to group virtual machines and define network security policies based on those groups. This also allows us to setup NSG Rules without restricting the Rules with specific IP Addresses and rather defining the rules based on ASG Names instead
Default NSG Rules
By Default there are certain Rules which cannot be removed from the Network Security Groups. However, these can be overridden by creating a Higher Priority Rule. Below are certain Default Rules
Inbound Rules
| Name | Priority | Source | Destination | Destination ports | Protocol | Access |
| AllowVNetInBound | 65000 | VirtualNetwork | VirtualNetwork | 0-65535 | Any | Allow |
| AllowAzureLoadBalancerInBound | 65001 | AzureLoadBalancer | 0.0.0.0/0 | 0-65535 | Any | Allow |
| DenyAllInbound | 65500 | 0.0.0.0/0 | 0.0.0.0/0 | 0-65535 | Any | Deny |
Outbound Rules
| Name | Priority | Source | Destination | Destination ports | Protocol | Access |
| AllowVnetOutBound | 65000 | VirtualNetwork | VirtualNetwork | 0-65535 | Any | Allow |
| AllowInternetOutBound | 65001 | 0.0.0.0/0 | Internet | 0-65535 | Any | Allow |
| DenyAllOutBound | 65500 | 0.0.0.0/0 | 0.0.0.0/0 | 0-65535 | Any | Deny |
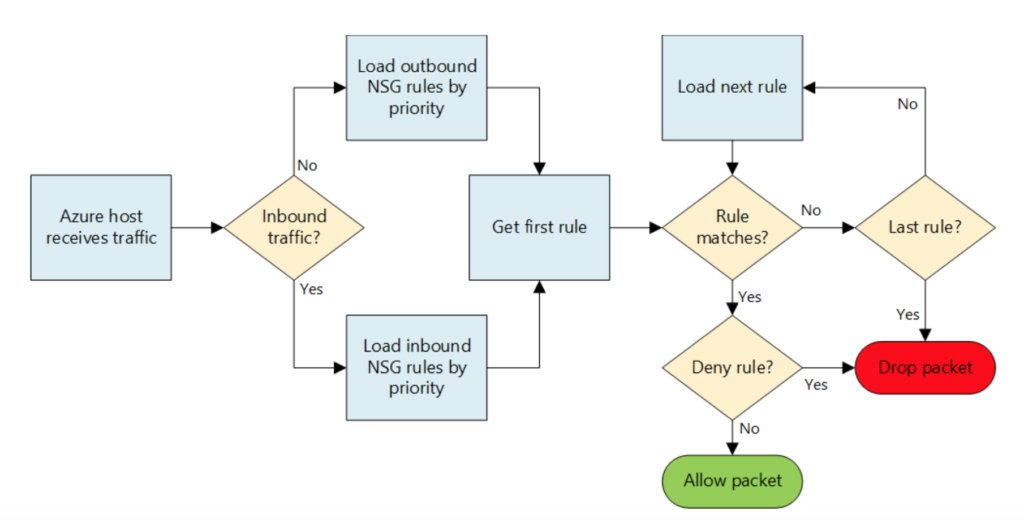
Here is how NSG Rules are processed
Happy Azure Networking !