Difference between Azure Application Gateway, Front Door, Azure Load Balancer & Azure Traffic Manager?
I have found Azure Cloud Architecture interesting and equally full of rich Products/ Features to cater to different Customer needs. I am going to focus this post on Load Balancing offerings by Azure. There are 2 basic Types based on Usage.
Application Load Balancing - This mostly runs on OSI Layer 7 and allows your to restrict and route path based routing. This also allows you to protect your applications against DDOS Attacks or SQL Injection. In this series there are 2 products from Azure. The Azure application Gateway and Azure Front Door.
DNS Based / IP Based Load Balancing - This mostly runs on OSI Layer 4 and allows your Backend aka Origin Servers to be routed the traffic based on 2-Tuple or 5-Tuple Network Routing Techniques. In this category there are 2 products namely Azure Load Balancer and Azure Traffic Manager. The Traffic Manager is basically a DNS Based load Balancer. More Details about DNS Load Balancing can be read here https://www.nginx.com/resources/glossary/dns-load-balancing/
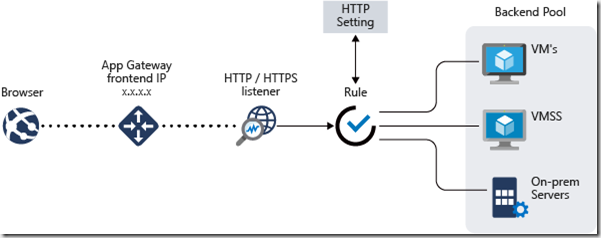
The Azure Application Gateway (AAG) is a web traffic manager for your web applications (one or multiple). With AAG, on top of load balancing your workloads, you can make routing decisions based on URI path or host headers. For example, you can route traffic based on the incoming URL. Therefore if /assets/images are in the inbound URL, you can route traffic to a specific set of servers (or pool) configured for images. If /video is in the URL, that traffic is routed to another pool.
The Azure Application Gateway includes a Web application firewall (WAF) which protects your backend / Origin Servers / Applications from common exploits like SQL injection attacks or cross-site scripting attacks
The Azure Application Gateway can also be used to do SSL Offloading technique of Load Balancing for Applications by just doing SSL hosting on Application gateway side however sending the Traffic to backend Servers unencrypted. This is OK in most cases, but it is not recommended due to eavesdropping which can happen from within your Network as well. Choose the SSL offloading feature at your risk.
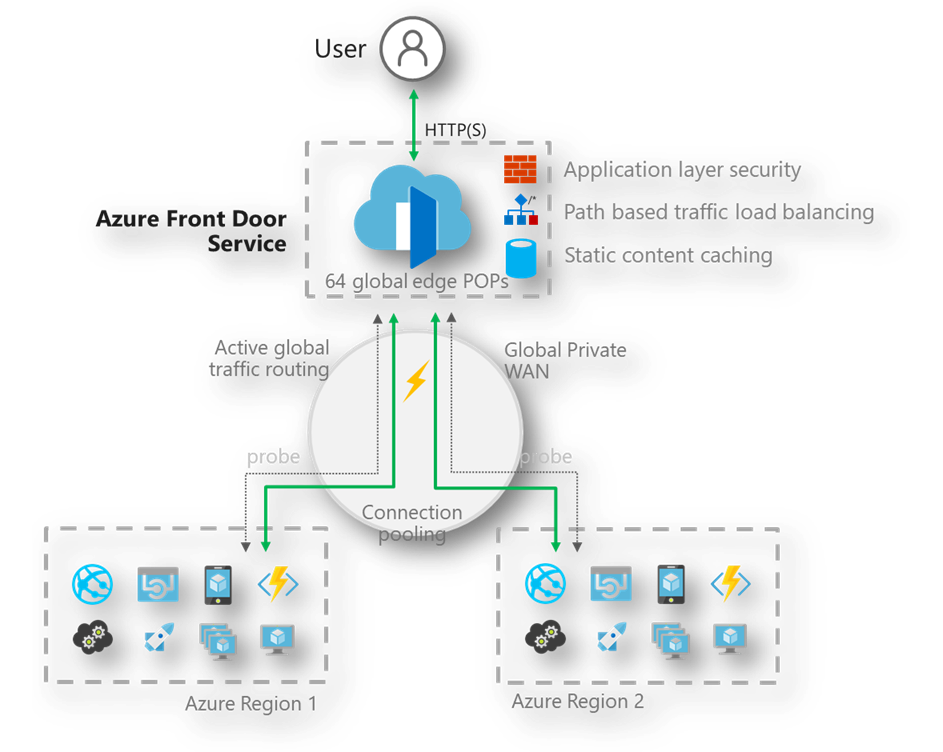
Azure Front Door allows to define, manage, and monitor the global routing for the web traffic (across regions).
It optimizes web traffic globally for performance (lowest latency) by using Edge Servers and POP Servers. This also allows for high-availability scenarios by enabling instant fail-over for all your Internet-facing applications hosted inside or outside of Azure.
It does so by using several traffic-routing methods (latency, Priority, weighted, and Session Affinity).
Just like the Azure Application Gateway Front Door can allow you to route traffic based on URL paths of the request but it does allow for more complex route matching scenarios
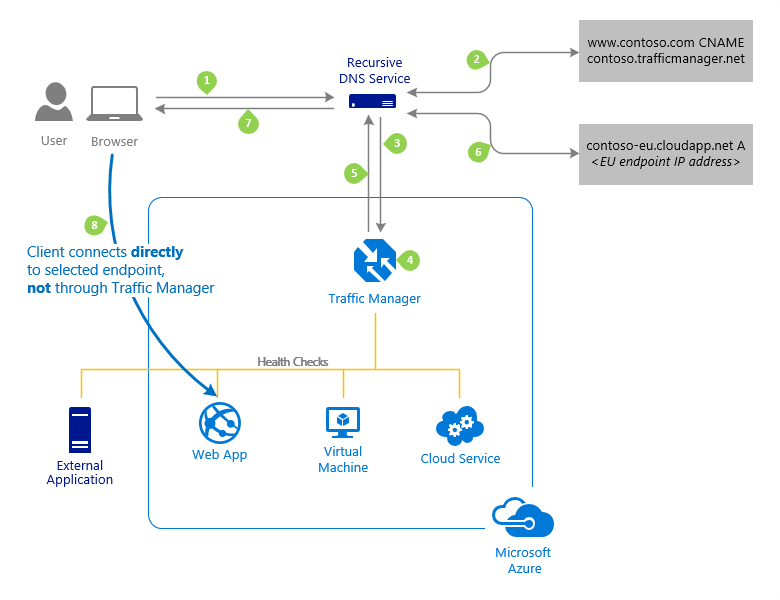
Azure Traffic Manager enables you to control the distribution of traffic across your application endpoints. An endpoint is any Internet-facing service hosted inside or outside of Azure.
The most important point to understand is that Traffic Manager works at the DNS level.
Traffic Manager uses DNS to direct clients to specific service endpoints based on the rules of the traffic-routing method. Clients connect to the selected endpoint directly.
Traffic Manager is not a proxy or a gateway. Traffic Manager does not see the traffic passing between the client and the service.
Load balancing refers to evenly distributing load (incoming network traffic) across a group of backend resources or servers.
Azure Load Balancer operates at layer four of the Network OSI model. It's the single point of contact for clients. Load Balancer distributes inbound flows that arrive at the load balancer's front end to backend pool instances.
Remember that Azure Load Balancer is not a physical device dedicated for you in your subscription or for your enterprise. The Azure Load Balancer is actually a way to “Reconfigure” the Azure Network in such a way that the Traffic is routed based on Load Balancing Health Probes and routes that you have configured.
These flows are according to configured load balancing rules and health probes. The backend pool instances can be Azure Virtual Machines or instances in a virtual machine scale set.
A public load balancer can provide outbound connections for virtual machines (VMs) inside your virtual network. These connections are accomplished by translating their private IP addresses to public IP addresses. Public Load Balancers are used to load balance internet traffic to your VMs.
An internal (or private) load balancer is used where private IPs are needed at the frontend only. Internal load balancers are used to load balance traffic inside a virtual network. A load balancer frontend can be accessed from an on-premises network in a hybrid scenario.
See you next week.